In theory, embedding database schema changes inside your application sounds like a shortcut to agility. You write the code, make the schema changes inline, and push it all together. It’s convenient, immediate, and seems to offer fast feedback. But in the real world—where stability, security, and collaboration matter—this practice becomes a liability.
The Illusion of Convenience
Many development teams fall into the trap of managing schema changes through their application code, treating the database as an extension of business logic. Frameworks and ORM tools even encourage this pattern by auto-generating migrations and executing them at runtime. It might feel like everything is automated and tidy.
But under the surface, this approach introduces fragility, creates audit and security blind spots, and destroys operational control.
Let’s unpack the dangers.
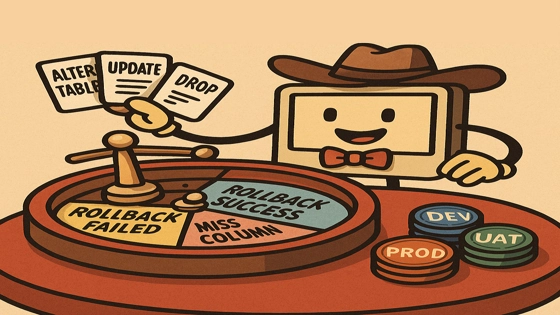
Why It’s Bad to Change the Database from Inside the Application
-
Lack of Version Control
Database schema changes done via app code often bypass version control best practices. Unlike code changes tracked via Git, inline DB updates may not be reviewed, tested, or even documented. There’s no reliable history, no diff view, and no ability to rollback gracefully.
-
Environment Drift Becomes Inevitable
As changes silently propagate through different environments (Dev, UAT, Staging, Prod), schema versions begin to diverge. Application A might auto-apply a change in Dev that never gets correctly reflected in Prod. Suddenly, the same app behaves differently in different environments.
Without centralized tracking and promotion of DB changes, environment parity becomes a myth.
-
Increased Time to Resolution During Failures
When something breaks, root cause analysis becomes a nightmare:
- Was it the app code?
- Was it the schema?
- Was it the sequence of updates?
- Was something missed in a previous environment?
This uncertainty increases downtime and slows recovery.
If rollback is required, it’s even worse. The app may revert to a previous version, but the DB schema—already mutated—stays ahead. Now you have mismatched expectations between code and schema.
-
Breaks the Separation of Concerns
Application code should handle logic and business rules. Infrastructure and data layers, like the database schema, require a different lifecycle, cadence, and ownership model. Mixing these responsibilities leads to confusion, poor collaboration, and unreliable systems.
-
Loss of Observability
When schema changes are embedded and executed at runtime, there’s no transparent log of what changed, when, by whom, and why. This impairs security audits, compliance reporting, and change tracking—all vital in regulated environments like finance, healthcare, or government.
-
Security & Permissions Risks
Apps typically run with limited permissions for a reason. Allowing them to alter schemas implies elevated access that can be misused, accidentally or maliciously. It violates the principle of least privilege and creates unnecessary attack surfaces.

-
Rollbacks Are a Gamble
Tight coupling of schema changes and app versions makes rollbacks almost impossible:
- Rolling back the app doesn’t rollback the schema.
- Some schema changes (like drops or alterations) are not easily reversible.
- The team might not even know what to rollback, or in what order.
-
No Accountability, No Control
When every app can change the DB, there’s no single source of truth. Everyone becomes a schema contributor without oversight. That leads to conflicts, duplication, inconsistent conventions, and schema chaos.
-
Inconsistent State Across Environments
If the DB change logic lives inside the app, each environment (Dev, UAT, Prod) is vulnerable to partial or failed changes. Schema updates can succeed in one place and fail in another, leading to silent inconsistencies that manifest as edge-case bugs or data corruption.
-
Collaboration Breakdown
DBAs, testers, compliance officers, and release managers are locked out of the loop. They can’t preview, validate, or approve changes because those changes are invisible until deployed. This undermines team alignment and shared accountability.
In the Real World, Schema Changes Need to Be Managed, Not Implied
Professionally run software delivery processes treat database changes as first-class citizens:
- Version-controlled
- Tested independently
- Promoted through controlled pipelines
- Approved and auditable
That’s where dedicated tools and platforms come in.
How DBmaestro Solves This Problem
DBmaestro provides an enterprise-grade solution to everything wrong with managing schema changes via application code. It transforms chaotic, app-driven database evolution into a controlled, visible, and governed process that fits perfectly into modern DevOps.
-
Centralized Version Control for the Database
All schema changes are tracked, versioned, and approved in a standard Git repo. You get:
- Full history of every change
- Who made it, when, and why
- Ability to compare versions and see diffs
This eliminates rogue changes and enables structured change promotion.
-
Controlled Promotion Across Environments
With DBmaestro, you define the path and rules for promoting schema changes:
- From Dev ➔ Test ➔ UAT ➔ Prod
- With gates, validations, and approvals at each stage
- Ensuring that all environments stay in sync and free of drift
No more surprises when deploying to production.
-
Automatic Drift Detection and Resolution
Drift between environments is automatically detected. DBmaestro shows exactly what is different between schemas, enabling teams to:
- Reconcile discrepancies quickly
- Avoid configuration drift issues
- Restore environment parity without manual guesswork
-
Safe Rollbacks and Change Auditing
Changes deployed through DBmaestro are rollback-capable. If something goes wrong, you can:
- Instantly revert to a known good state
- See exactly what changed
- Generate audit-ready compliance reports
This drastically reduces downtime and increases system reliability.
-
Built-in Security, Governance, and Compliance
With full audit trails, role-based access controls, and policy enforcement, DBmaestro ensures:
- Schema changes meet security policies
- No unauthorized access or privilege escalation
- Compliance requirements are met without added manual overhead
-
Decouples Application and Database Deployment
By treating the schema as an independent deployable, DBmaestro allows teams to:
- Release DB updates independently
- Avoid app-schema lockstep dependencies
- Support multiple apps sharing the same database safely
This is especially critical in microservices or enterprise environments with shared data layers.
-
Enables Real DevOps for the Database
With DBmaestro, the database becomes an active participant in CI/CD pipelines. You can:
- Integrate DB changes into Jenkins, Azure DevOps, GitLab, etc.
- Run pre-flight validations and approvals
- Enforce policies as code
- Monitor schema health and delivery KPIs
This aligns database work with the same agility and control as application delivery.
Conclusion
In the real world, where teams, tools, audits, and uptime matter, you don’t change your database schema from inside the application. That shortcut leads to fragility, chaos, and risk.
DBmaestro exists to solve this exact problem—turning the database into a managed, observable, and reliable part of your DevOps process. It provides the common ground where development, operations, and compliance can finally meet.
Because in the real world, software delivery isn’t just about moving fast. It’s about moving fast with control.